Managing a server is a demanding task that requires technical expertise, meticulous attention to detail, and strong organizational skills. Whether you’re operating a web server, business server, or gaming server, success hinges on implementing best practices in hardware selection, security, monitoring, and maintenance. In this guide, we’ll explore the essential steps needed to ensure optimal server performance, security, and reliability.
1. Choosing the Right Hardware and Software
The foundation of a well-functioning server starts with selecting the right hardware and software. Your choices should align with your server’s workload, expected traffic, and security requirements.
Key Hardware Considerations:
Processor (CPU): The processing power of your server determines how efficiently it can handle requests and execute tasks. High-performance servers often require multi-core processors or even dedicated server-grade CPUs like Intel Xeon or AMD EPYC.
Memory (RAM): Sufficient RAM ensures smooth multitasking and prevents slowdowns under heavy loads. The amount needed depends on your server type—database servers and virtualized environments demand significantly more RAM than basic web servers.
Storage: Fast and reliable storage is critical. Solid-state drives (SSDs) offer superior speed compared to traditional hard disk drives (HDDs), making them the preferred choice for high-performance applications.
Redundancy: Consider RAID (Redundant Array of Independent Disks) configurations to prevent data loss in case of a drive failure.
Scalability: Choose hardware that allows for future expansion as your server’s demands grow.
Key Software Considerations:
Operating System (OS): The OS should be selected based on compatibility with your applications. Linux distributions (e.g., Ubuntu Server, CentOS, Debian) are favored for web servers due to their stability and security, while Windows Server is common in enterprise environments.
Server Management Tools: Consider using control panels like cPanel, Plesk, or Webmin to simplify server management.
Security Software: Firewalls, intrusion detection systems (IDS), and malware protection are critical to safeguard your server against cyber threats.
Virtualization & Containerization: Tools like Docker and VMware allow for efficient resource utilization and easier deployment of applications.
2. Setting Up a Secure and Optimized Server Environment
Once you’ve selected the right hardware and software, it’s time to configure your server environment. Proper setup enhances security, performance, and overall reliability.
Network Configuration:
Assign static IP addresses for better stability and security.
Configure Domain Name System (DNS) settings correctly to ensure seamless connectivity.
Optimize bandwidth allocation to prevent bottlenecks, especially for high-traffic servers.
Firewall and Security Protocols:
Set up a firewall to restrict access to only necessary ports (e.g., block unused ports, limit SSH access to specific IP addresses).
Enable Secure Shell (SSH) key authentication for remote access instead of password-based logins.
Implement TLS/SSL certificates for encrypted communication (especially crucial for web servers).
Use two-factor authentication (2FA) for administrator accounts to add an extra layer of security.
Performance Optimization:
Enable caching mechanisms (e.g., Redis, Memcached) to reduce server load and speed up data retrieval.
Optimize database performance by indexing tables and running regular maintenance.
Fine-tune server configurations (e.g., adjusting PHP memory limits, setting up efficient query handling).
3. Monitoring Server Performance and Health
Continuous monitoring is essential to detect potential issues before they impact users.
Key Monitoring Areas:
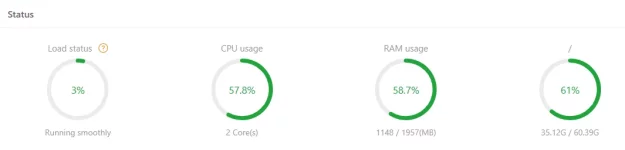
Resource Utilization: Track CPU, RAM, and disk usage to prevent overload and ensure optimal performance.
Uptime Monitoring: Use tools like UptimeRobot or Nagios to receive alerts when your server goes offline.
System Logs Analysis: Regularly review logs for unusual activity, failed login attempts, or hardware failures.
Load Testing: Simulate high-traffic conditions using tools like Apache JMeter to ensure your server can handle peak loads.
Recommended Monitoring Tools:
Prometheus & Grafana: Provides real-time analytics and visualization of server metrics.
New Relic & Datadog: Monitors application and infrastructure performance.
Fail2Ban: Automatically bans IPs engaging in suspicious activity.
4. Implementing a Robust Backup and Disaster Recovery Plan
Data loss can be catastrophic, making backups and recovery planning a top priority.
Backup Best Practices:
Regular Backups: Schedule automated backups at frequent intervals (daily for critical data, weekly for less crucial files).
Offsite Storage: Store backups in a secure offsite location or cloud-based storage to protect against hardware failures and disasters.
Incremental Backups: Use differential or incremental backups to reduce storage usage and speed up backup processes.
Encryption: Encrypt backups to prevent unauthorized access.
Disaster Recovery Planning:
Create a step-by-step recovery plan outlining how to restore your server in case of failure.
Test recovery procedures periodically to ensure backups are functional and restoration processes are efficient.
Have failover mechanisms like load balancers or secondary servers to maintain uptime during primary server failures.
5. Performing Routine Maintenance and Updates
Regular maintenance ensures server stability, security, and longevity.
Essential Maintenance Tasks:
Apply Security Patches: Keep your OS, applications, and firmware updated to prevent vulnerabilities.
Software Updates: Regularly update web servers (e.g., Apache, Nginx), database servers (e.g., MySQL, PostgreSQL), and other applications.
Disk Cleanup & Optimization: Remove unnecessary files, clear logs, and optimize databases to free up storage and enhance performance.
Check for Hardware Degradation: Monitor temperature levels, power supply health, and drive integrity to avoid unexpected failures.
Review User Access & Permissions: Regularly audit accounts and permissions to ensure proper security policies are enforced.
Conclusion: The Key to a Stable and Secure Server
Successfully running a server requires a combination of proactive security measures, continuous monitoring, and routine maintenance. By implementing the strategies outlined in this guide, you can ensure that your server operates efficiently, remains secure against threats, and provides a seamless experience for users.
Key Takeaways:
1. Choose the right hardware and software based on your workload and security requirements.
2. Secure your server environment with firewalls, encryption, and access controls.
3. Monitor performance metrics and logs to detect and resolve issues early.
4. Establish a backup and recovery plan to prevent data loss.
5. Perform regular updates and maintenance to keep the server stable and secure.
Staying up-to-date with evolving technologies and best practices in server administration will further enhance your ability to manage and optimize your server effectively. By maintaining a structured approach to server management, you can build a reliable, high-performance infrastructure that supports your business or community’s needs.
1. Choosing the Right Hardware and Software
The foundation of a well-functioning server starts with selecting the right hardware and software. Your choices should align with your server’s workload, expected traffic, and security requirements.
Key Hardware Considerations:
Processor (CPU): The processing power of your server determines how efficiently it can handle requests and execute tasks. High-performance servers often require multi-core processors or even dedicated server-grade CPUs like Intel Xeon or AMD EPYC.
Memory (RAM): Sufficient RAM ensures smooth multitasking and prevents slowdowns under heavy loads. The amount needed depends on your server type—database servers and virtualized environments demand significantly more RAM than basic web servers.
Storage: Fast and reliable storage is critical. Solid-state drives (SSDs) offer superior speed compared to traditional hard disk drives (HDDs), making them the preferred choice for high-performance applications.
Redundancy: Consider RAID (Redundant Array of Independent Disks) configurations to prevent data loss in case of a drive failure.
Scalability: Choose hardware that allows for future expansion as your server’s demands grow.
Key Software Considerations:
Operating System (OS): The OS should be selected based on compatibility with your applications. Linux distributions (e.g., Ubuntu Server, CentOS, Debian) are favored for web servers due to their stability and security, while Windows Server is common in enterprise environments.
Server Management Tools: Consider using control panels like cPanel, Plesk, or Webmin to simplify server management.
Security Software: Firewalls, intrusion detection systems (IDS), and malware protection are critical to safeguard your server against cyber threats.
Virtualization & Containerization: Tools like Docker and VMware allow for efficient resource utilization and easier deployment of applications.
2. Setting Up a Secure and Optimized Server Environment
Once you’ve selected the right hardware and software, it’s time to configure your server environment. Proper setup enhances security, performance, and overall reliability.
Network Configuration:
Assign static IP addresses for better stability and security.
Configure Domain Name System (DNS) settings correctly to ensure seamless connectivity.
Optimize bandwidth allocation to prevent bottlenecks, especially for high-traffic servers.
Firewall and Security Protocols:
Set up a firewall to restrict access to only necessary ports (e.g., block unused ports, limit SSH access to specific IP addresses).
Enable Secure Shell (SSH) key authentication for remote access instead of password-based logins.
Implement TLS/SSL certificates for encrypted communication (especially crucial for web servers).
Use two-factor authentication (2FA) for administrator accounts to add an extra layer of security.
Performance Optimization:
Enable caching mechanisms (e.g., Redis, Memcached) to reduce server load and speed up data retrieval.
Optimize database performance by indexing tables and running regular maintenance.
Fine-tune server configurations (e.g., adjusting PHP memory limits, setting up efficient query handling).
3. Monitoring Server Performance and Health
Continuous monitoring is essential to detect potential issues before they impact users.
Key Monitoring Areas:
Resource Utilization: Track CPU, RAM, and disk usage to prevent overload and ensure optimal performance.
Uptime Monitoring: Use tools like UptimeRobot or Nagios to receive alerts when your server goes offline.
System Logs Analysis: Regularly review logs for unusual activity, failed login attempts, or hardware failures.
Load Testing: Simulate high-traffic conditions using tools like Apache JMeter to ensure your server can handle peak loads.
Recommended Monitoring Tools:
Prometheus & Grafana: Provides real-time analytics and visualization of server metrics.
New Relic & Datadog: Monitors application and infrastructure performance.
Fail2Ban: Automatically bans IPs engaging in suspicious activity.
4. Implementing a Robust Backup and Disaster Recovery Plan
Data loss can be catastrophic, making backups and recovery planning a top priority.
Backup Best Practices:
Regular Backups: Schedule automated backups at frequent intervals (daily for critical data, weekly for less crucial files).
Offsite Storage: Store backups in a secure offsite location or cloud-based storage to protect against hardware failures and disasters.
Incremental Backups: Use differential or incremental backups to reduce storage usage and speed up backup processes.
Encryption: Encrypt backups to prevent unauthorized access.
Disaster Recovery Planning:
Create a step-by-step recovery plan outlining how to restore your server in case of failure.
Test recovery procedures periodically to ensure backups are functional and restoration processes are efficient.
Have failover mechanisms like load balancers or secondary servers to maintain uptime during primary server failures.
5. Performing Routine Maintenance and Updates
Regular maintenance ensures server stability, security, and longevity.
Essential Maintenance Tasks:
Apply Security Patches: Keep your OS, applications, and firmware updated to prevent vulnerabilities.
Software Updates: Regularly update web servers (e.g., Apache, Nginx), database servers (e.g., MySQL, PostgreSQL), and other applications.
Disk Cleanup & Optimization: Remove unnecessary files, clear logs, and optimize databases to free up storage and enhance performance.
Check for Hardware Degradation: Monitor temperature levels, power supply health, and drive integrity to avoid unexpected failures.
Review User Access & Permissions: Regularly audit accounts and permissions to ensure proper security policies are enforced.
Conclusion: The Key to a Stable and Secure Server
Successfully running a server requires a combination of proactive security measures, continuous monitoring, and routine maintenance. By implementing the strategies outlined in this guide, you can ensure that your server operates efficiently, remains secure against threats, and provides a seamless experience for users.
Key Takeaways:
1. Choose the right hardware and software based on your workload and security requirements.
2. Secure your server environment with firewalls, encryption, and access controls.
3. Monitor performance metrics and logs to detect and resolve issues early.
4. Establish a backup and recovery plan to prevent data loss.
5. Perform regular updates and maintenance to keep the server stable and secure.
Staying up-to-date with evolving technologies and best practices in server administration will further enhance your ability to manage and optimize your server effectively. By maintaining a structured approach to server management, you can build a reliable, high-performance infrastructure that supports your business or community’s needs.